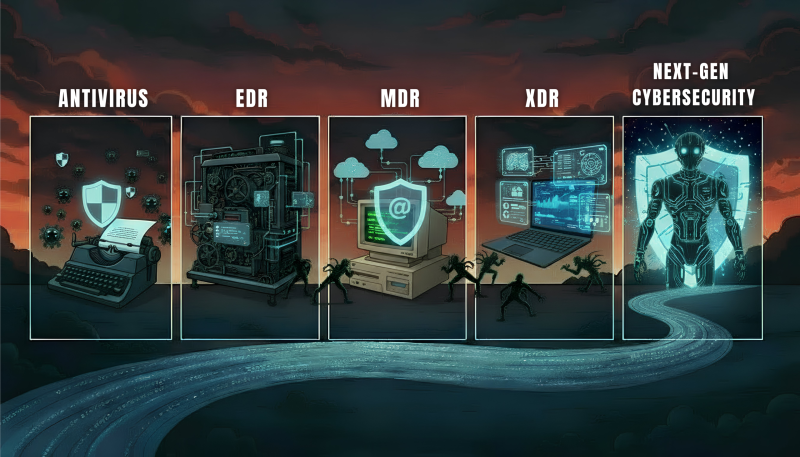
As cyber threats evolved, so did cybersecurity. Yet attackers keep finding new ways in.
It’s the early 2010s – EDR
Companies are faced with more sophisticated attacks – and realizing that traditional antivirus tools are not filling the bill. Antivirus could only stop threats that were already known and defined, often after it was too late. Companies needed real-time visibility into their endpoints – the physical devices connected to a network, like desktops, laptops, servers and virtual machines.
This gave rise to Endpoint Detection and Response (EDR). The new EDR software continuously monitored endpoint activity, collected data, and allowed company personnel to detect, investigate, and remediate the latest advanced attacks. But EDR generated massive volumes of alerts that required handling by a highly trained security staff.
It’s the mid-2010s – MDR
Companies, especially small and mid-sized businesses, realized they didn’t have the internal expertise and 24/7 coverage they needed to manage EDR effectively. This produced a new cybersecurity concept: Managed Detection and Response (MDR). MDR filled the gap through outsourced security operations centers (SOCs) “as-a-service.” These external security teams monitored systems around the clock and handled detection and response actions on behalf of clients.
It’s around 2020 – XDR
Organizations face the next big cybersecurity challenge – protecting their expanding IT layers like multiple networks, email systems, and user identities. Extended Detection and Response (XDR) evolved to unify all this divergent information onto a single platform. XDR integrated functions like EDR, SIEM (centralized data on threats and alerts), and SOAR (responses to threats). This combination resulted in faster and smarter detection and analysis, with automated, multi-layered responses.
It’s today – and we must move forward from traditional MDR/XDR
While MDR/XDR seems like the best current solution, they have their own inherent limitations that attackers are exploiting, and breaches continue. Challenges include:
* The focus is still on an organization’s known managed devices and known endpoints; this can leave blind spots in the external attack surface
* Data from non-endpoint sources is often missed; this data gap slows detection and misinforms responses
* There’s still a reactive posture – waiting for alerts instead of preventing threats
* The use of periodic (vs. continuous) scans leaves exploitable windows between assessments
* The business risks or threat prioritization of attacks are often lacking or without context
So, what’s needed in the next evolution of cybersecurity?
* Total asset coverage – mapping the complete environment and uncovering vulnerabilities, including cloud, IoT, shadow IT, and unmanaged infrastructure
* Continuous vulnerability assessments – detecting and automating, in real time, the verification of fixed vulnerabilities or neutralized security threats (remediations)
* Use of AI – combining AI with the human expertise in the SOC
* Comprehensive data analysis – collecting millions of signals across the company’s full digital environment
* Proactive threat hunting – enforcing zero-trust access and proactively identifying threats before they breach
* Respond and learn – automating responses and adapting with real-time intelligence
We’ve seen the evolution from antivirus to EDR to MDR and XDR. As the attackers get more sophisticated, organizations themselves must get more sophisticated with their cybersecurity – it’s what’s next.
How Guardian can help
Guardian goes beyond MDR/XDR with its PrismX. This is a full-spectrum cybersecurity platform that combines zero-trust enforcement with proactive threat intelligence. It continuously protects beyond just your managed endpoints to include your entire digital footprint by integrating always-on vulnerability scanning with hunter-led detection across cloud, IoT and shadow assets. The PrismX AttackSOC utilizes AI and our people’s know-how to hunt down threats before they strike. Don’t rely on yesterday’s defense model. Talk to our team and explore the PrismX platform.
The Guardian difference
Defender and attacker – that’s how Guardian works. Our proactive red and reactive blue teams work together as one defense to hunt threats, identify gaps, and stop breaches before they start. We don’t replace your IT provider or MSP agreement; we work alongside them to provide what they can’t. Why? Because cybersecurity is a hard, ever-changing environment. And anyone who tells you it’s simple, or that they already have you covered as part of other managed services, doesn’t understand today’s high-level threat landscape. We do understand – and that’s the Guardian difference.
Don’t leave your organization exposed. Learn how PrismX provides total visibility, proactive threat hunting, and AI-powered protection across every asset. Get your full PrismX guide here.